People and process
Terraform is not just a standalone tool: its effective use requires thoughtful allocation of staff resources and processes to achieve a notable return on investment.
Implementing quick changes to people and processes can be difficult due to cultural and political dynamics. Understanding the underlying concepts and reasons is crucial. Being practical is vital since modifying an organizational structure is gradual, and adjustments will likely be needed to fit specific requirements.
This section delves into key organizational ideas that our customers have found valuable for deploying Terraform effectively and embracing the Cloud Operating Model discussed earlier.
Modern operations framework
Adopting the Cloud Operating Model is essential due to today's widespread use of cloud computing. The API model for consuming infrastructure, championed by the release of AWS S3 in 2006, required a new way to orchestrate the management of infrastructure components, and IaC quickly emerged as the most efficient approach. Terraform (introduced in 2014) stood out as a best-of-breed tool in this area.
With annual cloud spend nearly $100 billion by 2016, and many business critical workloads running in the cloud, companies needed guardrails to control cloud infrastructure deployment, but they also had to offer cloud-enabled services to customers quickly to maintain competitive advantage.
In this context, HashiCorp introduced the Cloud Operating Model, which allows organizations to industrialize cloud adoption and reconcile those seemingly opposing goals.
Organizing for industrialized cloud adoption
We see many of our customers adopting an industrialized IT operations framework composed of a number of functions fulfilled by one or more teams. The following diagram illustrates the key functions and how they relate to each other.
Note
The diagram below is tuned to our current context of infrastructure provisioning.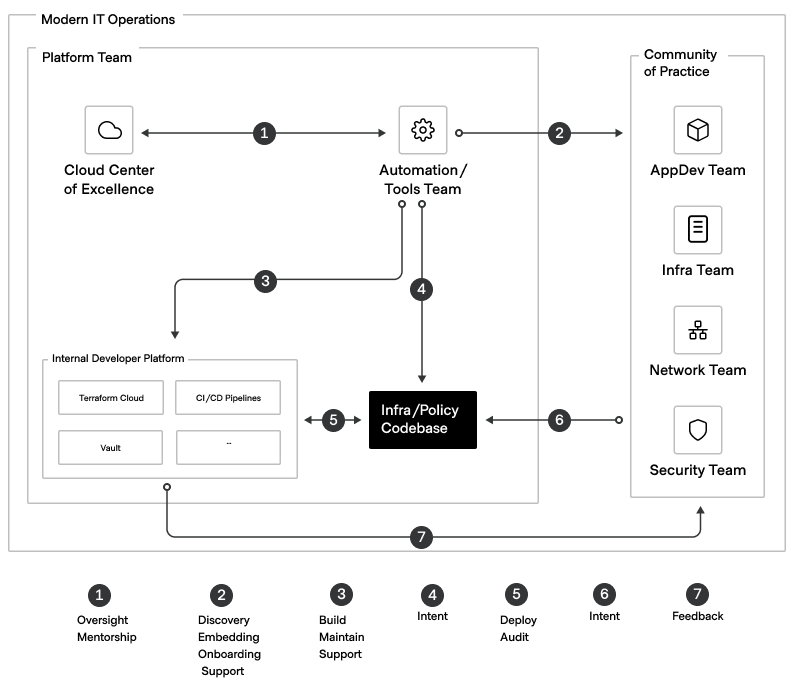
Platform Team
The Platform Team serves as the central hub within the organization, orchestrating various functions and ensuring streamlined operations across teams. It may be composed of one or more teams whose functions encompass several key roles, including:
Cloud Center of Excellence (CCoE): This strategic arm of the Platform Team drives cloud adoption and aligns cloud strategies with business objectives. The CCoE establishes governance frameworks, fosters knowledge sharing, and optimizes cloud resources to maximize value and ensure compliance.
Automation/Tools: As a tactical component of the Platform Team, this function manages essential tools and automation to support efficient system operations. It implements golden workflows and reusable modules, collaborating with stakeholders to ensure that services meet consumer needs and align with strategic directives. This may or may not be a separate sub-team.
IaC/PaC: The Platform Team sets the intent for infrastructure-as-code and policy-as-code, collaborating with security to ensure adherence to standards and best practices. This promotes standardization, scalability, and compliance across projects.
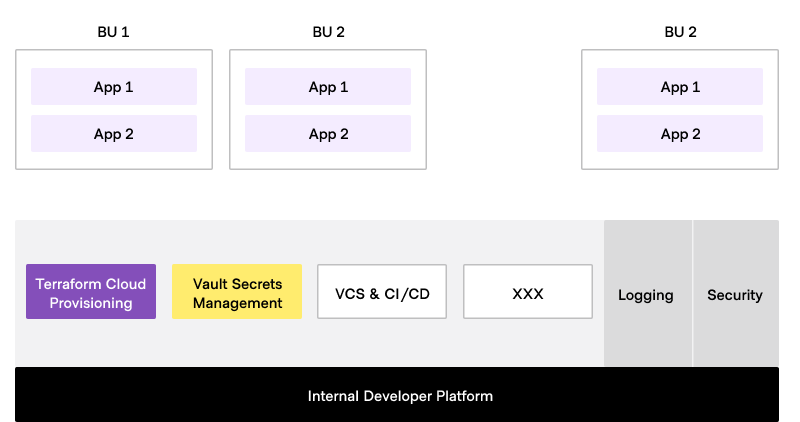
Internal Developer Platform (IDP): Facilitated by the Platform Team, this streamlines development cycles and reduces organizational complexity. It leverages a product management approach, allowing development teams to consume golden paths in a self-service mode, thereby enhancing productivity and efficiency.
Note
While we talk of the Platform Team as a singular team, it is possible that it is composed of multiple teams with separate areas of responsibility e.g. secrets management might be owned by a separate team from infrastructure provisioning. These teams will however collaborate closely to ensure that developers in the various application teams have easy access to these shared services.
Security team
The Security team collaborates with the Platform Team to establish governance policies and deploy monitoring tools for securing cloud-based infrastructure. They implement security controls around network segmentation, access management, and encryption to prevent unauthorized access and data breaches.
Ensuring compliance with regulations and internal policies is a key focus, with the team conducting audits and enforcing security policies. They integrate security controls into CI/CD pipelines, scanning code and images for vulnerabilities.
Identity and access management (IAM) is prioritized, with the team managing user identities and permissions to minimize the risk of unauthorized access. Data security measures include encryption, data classification, and data loss prevention to protect sensitive data.
In threat detection and incident response, the team sets up monitoring systems and intrusion detection tools to swiftly respond to security incidents, minimizing impact and ensuring resolution.
Cloud security is a function of the security team; this function ensures HCP Terraform security aligns with organizational policies by:
- Subscribing to security updates & vulnerability alerts and collaborating with SRE to apply patches as needed.
- Managing TLS certificate validity and renewal for TFE, ensuring trust with integrations.
- Regularly scanning TFE instances for vulnerabilities and integrating SIEM tools for audit logging.
- Providing governance inputs to CCoE, including defining and enforcing PaC guardrails and maintaining standards such as CIS benchmarks.
In collaboration with the Platform Team, they enforce security controls and conduct acceptance reviews to enhance platform security.
Note
IaC governance/Sentinel is covered as part of a the Standardize HVD.Producers/consumers
In a shared service model, producers configure the system to meet consumer needs and consumers utilize shared services provided by the Platform Team.
Producers' Responsibilities:
- Provide seamless onboarding to the HCP Terraform platform.
- Manage the private registry.
- Oversee Policy-as-Code (PaC) implementation.
- Offer necessary enablement to consumers.
Consumers' Responsibilities:
- Initiate requests for access to the HCP Terraform platform.
- Write Terraform code based on available private registry modules and recommended practices established by the Platform Team.
- This collaboration ensures that shared services are readily accessible and efficiently utilized, unlocking the benefits of the HCP Terraform platform while meeting specific business needs and adhering to set guidelines and standards.
Organizational big picture
The hierarchy of application teams and platform teams can vary depending on the organization. In some organizations, such as those in banking, telecommunications, and healthcare, application teams may fall under a completely different hierarchy than the Platform Team. In other organizations, such as those focused on technology products, the application teams and platform teams may be part of the same hierarchy.
Other organizational functions, including finance and security, provide governance inputs to the Platform Team and will request reporting and feedback to measure how effectively the governance is being applied.
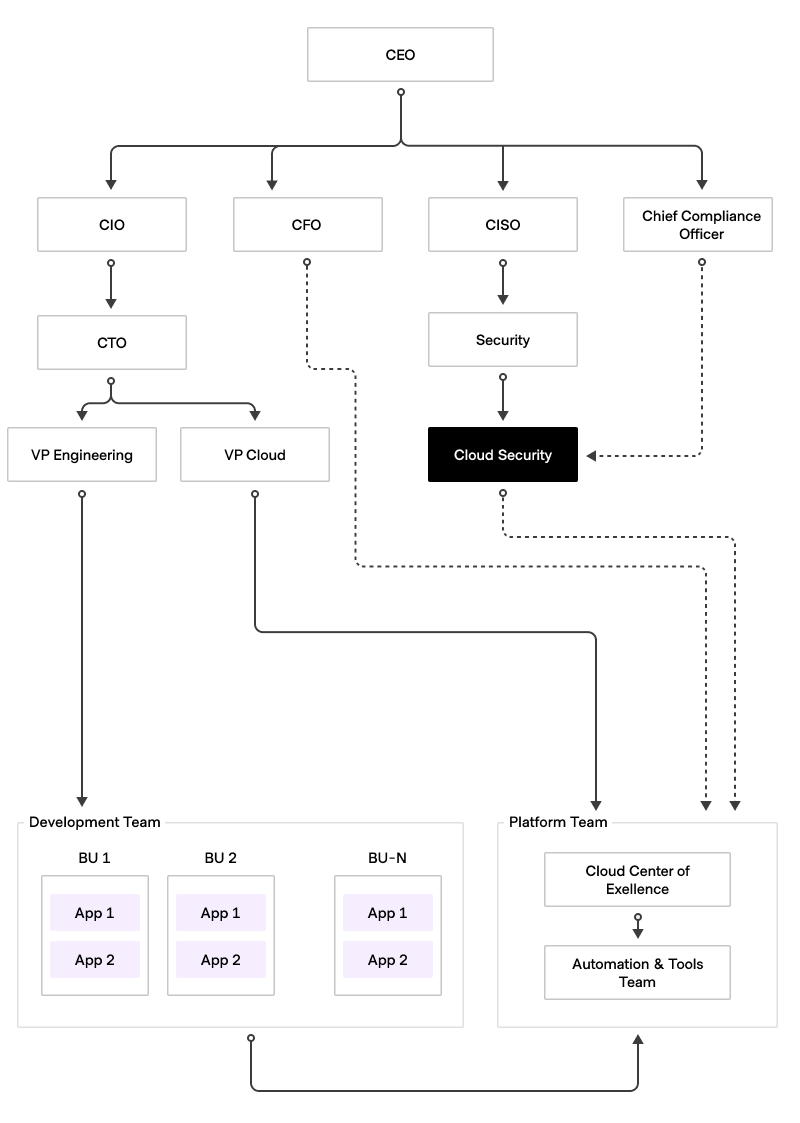
By centralizing expertise, fostering collaboration, and implementing best practices, the Platform Team accelerates time-to-market, enhances security, and drives innovation within the organization.
Golden IaC workflows
A golden workflow is a standardized, repeatable process for completing a specific task or achieving a specific outcome. It is typically well-documented and tested, and it is designed to be efficient and effective. Golden workflows are often used in DevOps and provide:
- Facilitate automation
- Improve efficiency, productivity, consistency, quality, communication and collaboration
- Reduce errors, onboarding time, and time-to-market for software components
Using pre-approved Terraform configurations and curated modules, the Platform Team shifts these golden workflows left, empowering teams to independently provision infrastructure resources while maintaining centralized management and control using best practices. The following diagram illustrates the golden workflow.
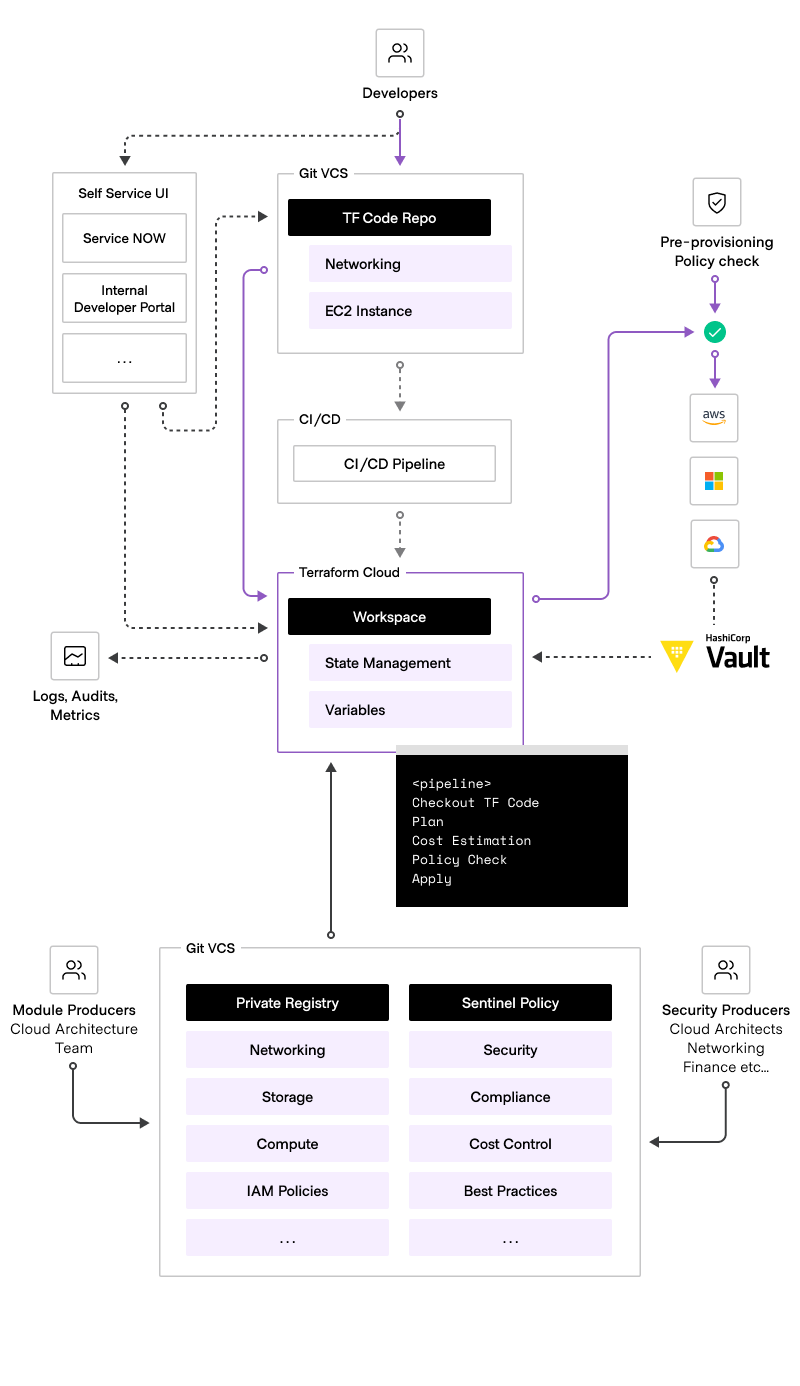
Within these golden workflows, there are typically two aspects:
- Producer workflows
- Module development - to create Terraform modules and register them with the private registry.
- PaC development - to develop Sentinel/OPA code and registering the policies they constitute in HCP Terraform.
- Consumer workflows
- Landing zone workflow - to provision cloud accounts/credentials and core Terraform configuration elements from reusable modules. This also deploys relevant VCS respositories and HCP Terraform projects and workspaces.
- Developer workflow - to facilitate the creation of IaC relevant to support the application components under remit.