Terraform Secrets Engine
As adoption of HCP Terraform grows, you may look at incorporating it into your automated workflows and existing tooling. Interaction with the HCP Terraform API relies on auth tokens generated by the API and used by external systems to automate actions in HCP Terraform, often as part of an organization’s CI/CD pipelines. Operators are left with the responsibility of tracking which tokens are in-use by their organizations.
The Vault Terraform Cloud secrets engine(opens in new tab) enables you to generate, manage and revoke credentials for HCP Terraform and Terraform Enterprise while adhering to best practices of access and control.
It is recommended that API driven workflows in your organization leverage the dynamic HCP Terraform API token generated by Terraform Cloud secrets engine. The lifecycle of these tokens is managed by Vault and will auto expire according to the configured TTL and max TTL of the Vault role.
Here is an example pattern of a VCS CI/CD pipeline leveraging this workflow:
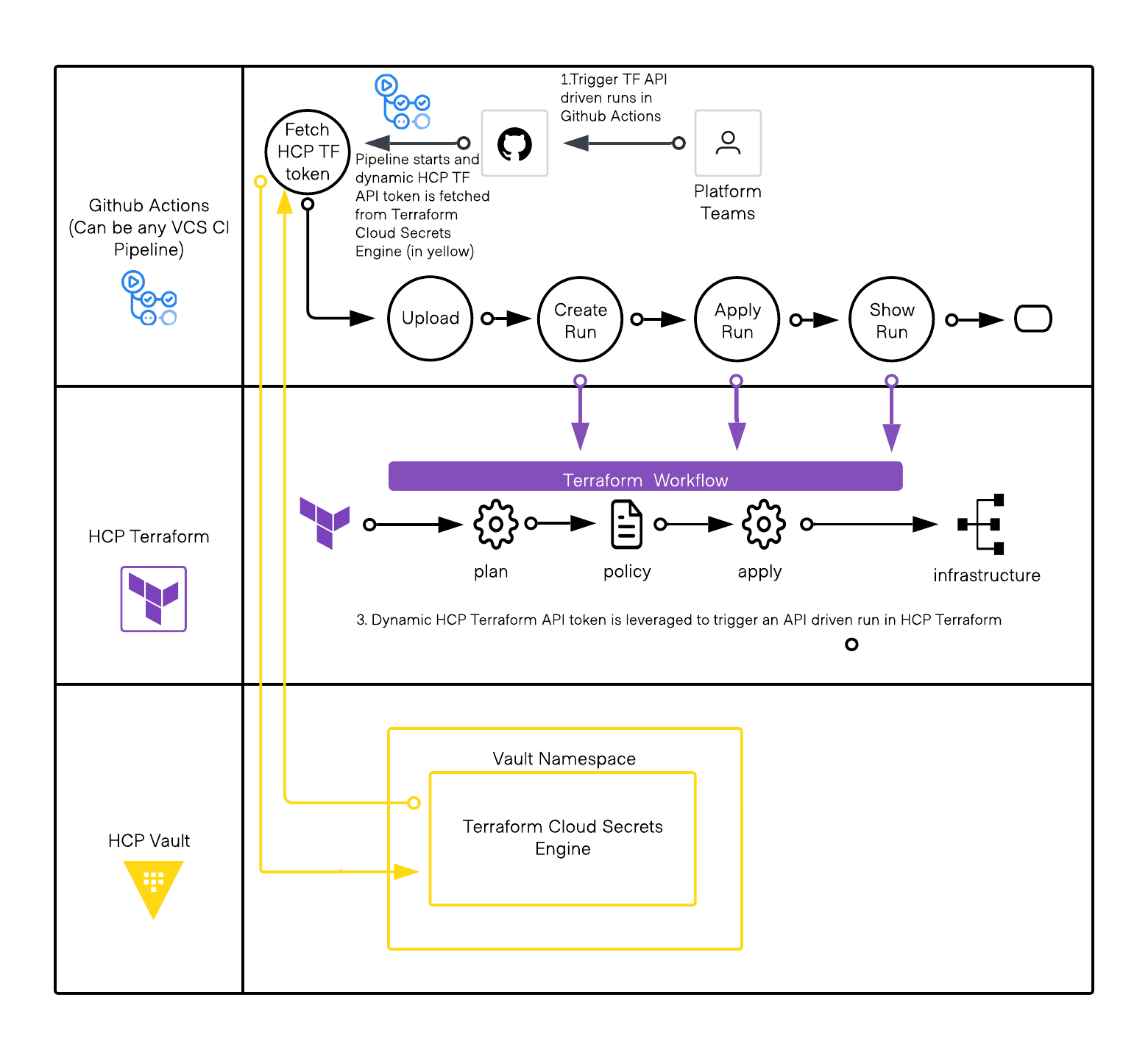
- Platform teams trigger an API driven workflow in the VCS CI/CD pipeline.
- As an initial step, a stage in the pipeline fetches a dynamic HCP Terraform API token from Vault based on the use case.
- This dynamic HCP Terraform API token is then leveraged to trigger an API driven workflow in a HCP Terraform workspace and the plan and apply stages of the run proceed.
The HCP Terraform API limits both organization and team roles to one active token at any given time. Generating a new organization or team API token by reading the credentials in Vault or otherwise generating them on app.terraform.io (or your Terraform Enterprise FQDN) will effectively revoke any existing API token for that organization or team.
Due to this behavior, organization and team API tokens created by Vault will be stored and returned on future requests, until the credentials get rotated. This is to prevent unintentional revocation of tokens that are currently in-use.