Packer: Push containers to cloud repositories
| HashiCorp products | HCP Packer |
|---|---|
| Partner products | AWS ECR, GCP Artifact Registry, Azure Container Registry |
| Maturity model | Adoption |
| Use case coverage | Deployment of application artifacts |
| Tags | Packer, Docker, AWS, GCP, Azure, Containers, Docker |
| Guide type | HVD integration guide |
| Publish Date, version | 08/06/2024, version 1.0.0 |
| Authors | Bruce Harrison |
Introduction
Prescriptive guidance
Our objective in these HashiCorp Validated Designs is to give you prescriptive, best practice guidance based on our experience partnering with numerous organizations who have implemented HCP Terraform with HCP Packer.
Note
This guide makes use of both Packer OSS and the HCP Packer platform:
- Packer OSS is the CLI tool used to build containers and VM images
- HCP Packer is a SaaS product that stores container and VM metadata generated by Packer OSS
This guide will help you with creating and managing Docker containers via HCP Packer and interface them with various CSP container registries. This guide will demonstrate how to push images to AWS, Azure, and GCP container registries.
Target audience
- DevOps User
HCP Packer container push process
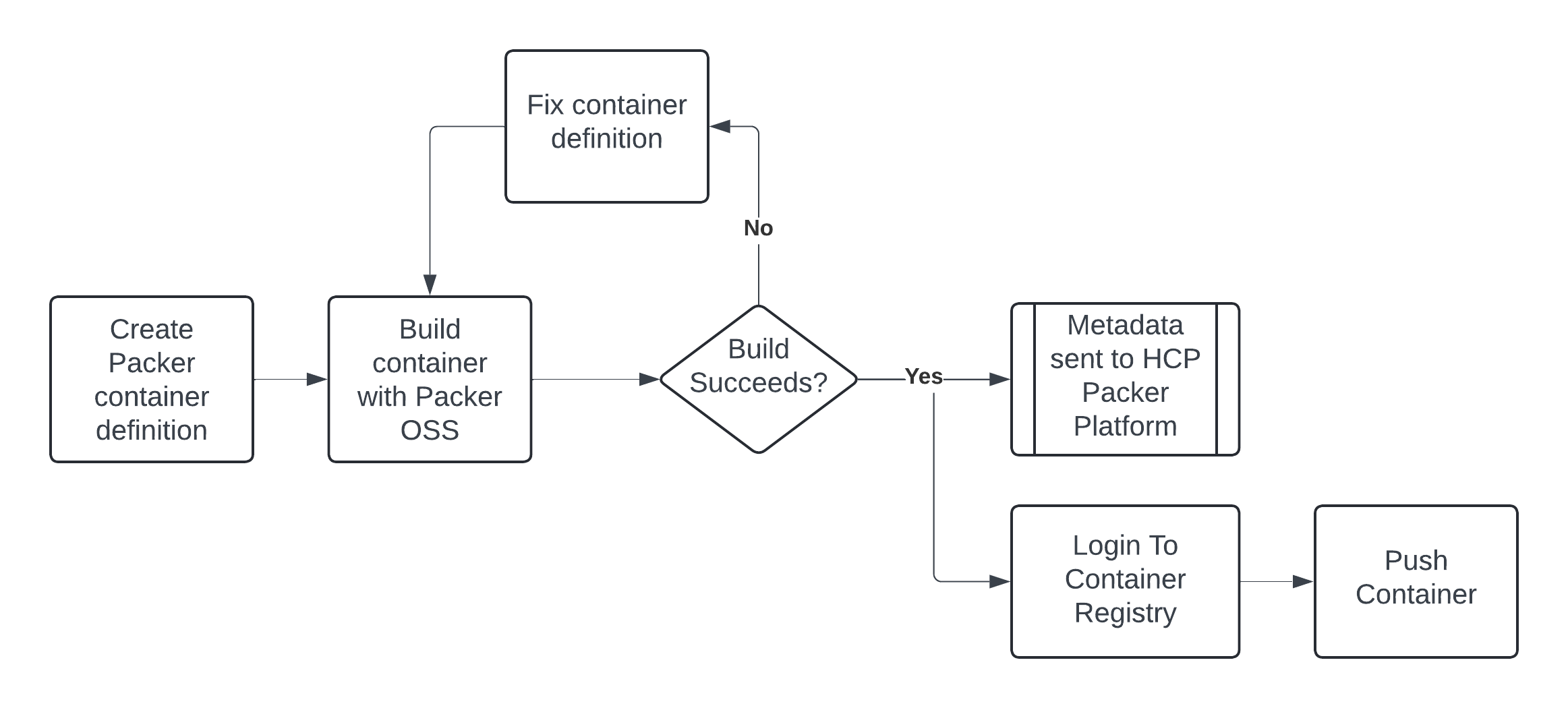
Benefits
The principal benefits of using HCP Packer to build containers instead of the standard Docker CLI are as follows:
- Capturing of container metadata by the HCP platform
- Visibility into container lineage
- Notification when a derived image is outdated due to a new version of the parent being released
- Leverage HCP Packer webhooks for more advanced CSP registry management
- VM images and containers can share a common declarative file format (Packer HCL) that is used to describe and build both.
Considerations
- This document focuses on running this process from a local machine, but the same concepts could easily be applied to a CI/CD mechanism such as Github Actions or Gitlab Runners.
- IaC such as Terraform should be used to provision the underlying infrastructure.
- Examples for deploying with each cloud platform's CLI are also provided.
- Due to the way Packer post-processors and Docker login works, if you plan on pushing images to multiple CSPs, they should each be run in an isolated context.
- Attempting to push multiple images in parallel from a single context can cause transient failures as they all compete for
docker loginaccess.
- Attempting to push multiple images in parallel from a single context can cause transient failures as they all compete for
- Packer offers a docker-push post processor, but we will not be using it in this guide.
- The post-processor is inherently inflexible, and causes wide divergence in container push processes across CSPs.
- For the sake of keeping things simple in this guide, we will not be using it and instead will be manually logging into registries and pushing the containers.
- This method is broadly applicable to CI/CD scenarios as well.
- Every CSP has unique constraints on how credentials are handled.
- We use long-lived credentials in these examples for brevity, but this may not work for all organizations.
- Implementers should consult with their internal security teams to ensure that the CSP authentication method aligns with company policies and practices.
Prerequisites
- Access to at least one CSP (AWS, GCP, Azure).
- CLI tooling for at lest one CSP (AWS, GCP, Azure).
- Ensure that you have the necessary permissions to create resources within your chosen CSP.
- Have a working Packer HCL file configured for building a Docker container.
- Packer OSS CLI >=v1.11.0 installed (see documentation(opens in new tab)).
- An existing HCP Packer Account (HCP Platform(opens in new tab)).
- Git CLI installed (HCP Platform(opens in new tab)).
- An active HCP service principal(opens in new tab).
Related resources
- Packer installation instructions(opens in new tab)
- Packer docker-push Post Processor(opens in new tab)
- HCP Packer Registry metadata block(opens in new tab)
- Push metadata to HCP Packer(opens in new tab)